A simple software update gone awry led to one of the largest IT outages in history.
While the issue originated at cybersecurity company CrowdStrike, it had across-the-board impacts on global IT systems, disrupting operations in critical sectors from airlines and banks to emergency services. Many organizations are now asking: How could a single software update cause such widespread disruption, and what measures could have helped reduce the impact of the fallout?
Let's explore why this incident reinforces the need for more robust risk management to enhance digital resilience and how emerging regulations like DORA and NIS2 are driving urgency.
A widening risk landscape
Organizations increasingly rely on third parties to drive innovation and competitiveness. However, the lack of visibility across third and even fourth parties adds complexity to managing risk and driving operational resilience, making it even more difficult to demonstrate compliance.
A single breach or failure can reverberate throughout the supply chain, impacting those organizations close to or indirectly connected to a vendor or supplier. This highlights the critical need to identify and manage not only third parties but also trace the risks concentrated in fourth and nth parties.
The CrowdStrike outage highlights the importance of regulations like DORA to strengthen operational resilience practices
DORA is a mandatory EU regulation designed to improve the financial industry's resilience against ICT (Information and Communication Technology) disruptions. It joins other regulations, such as NIS2, FCA, and LkSG, aiming to strengthen operational resilience.
However, there's a key distinction: The Act's inclusion of ICT third-party risk within the overall risk management framework holds financial entities and their business partners accountable for downstream risks across third, fourth, and nth parties.
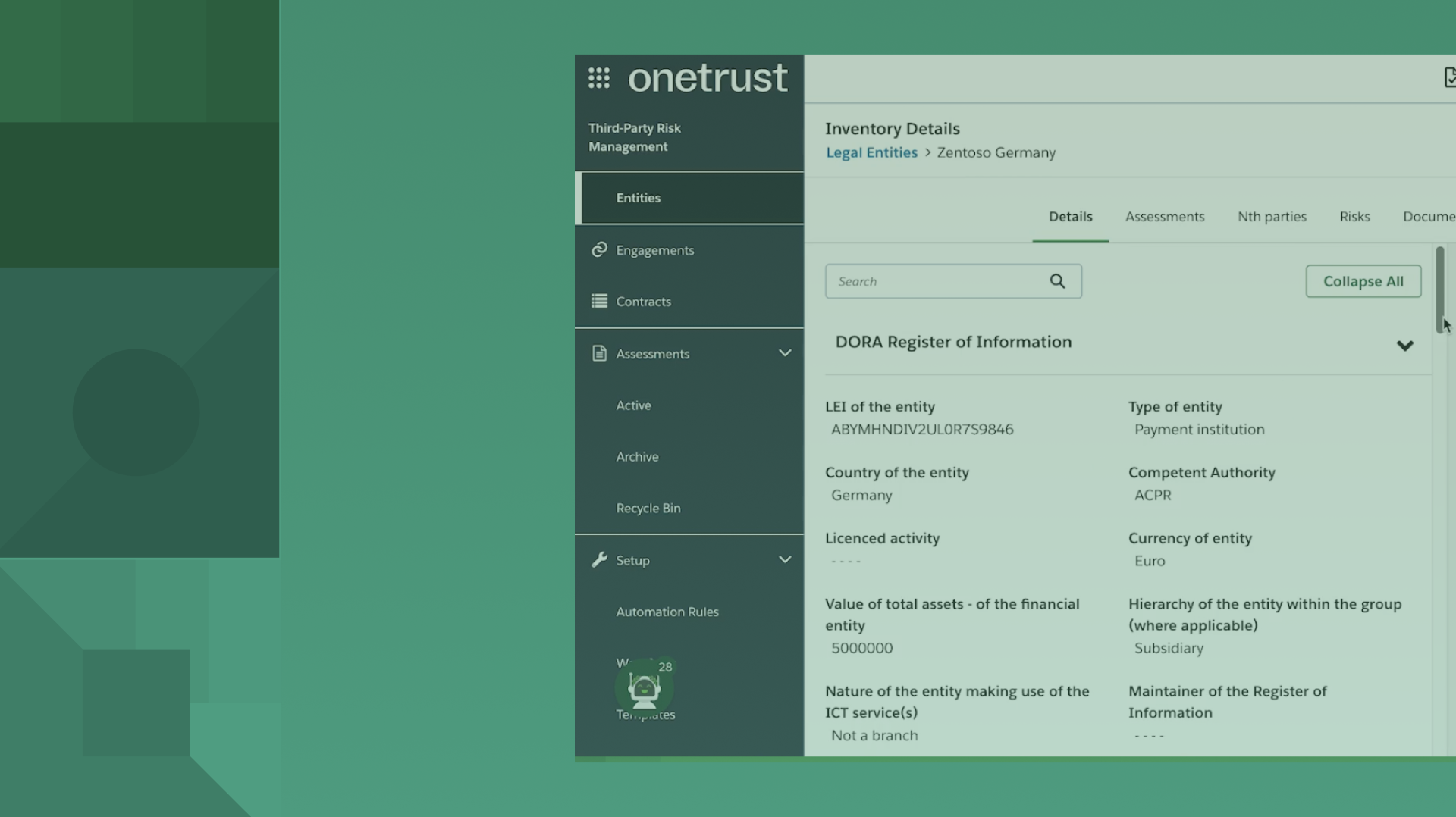
For example, DORA requires financial entities to continuously monitor and oversee third-party service providers to ensure compliance with contractual commitments and manage risks per commitment. In the event of an incident, they must put processes in place to manage and report on their third-party service provider.
Build operational resilience with OneTrust
After the CrowdStrike incident, digital operational resilience will come into sharper focus. It highlights the growing reliance on third-party providers in today’s world and the need for organizations to build resiliency when digital supply chain systems fail.
Upcoming EU regulations like DORA and NIS2 will start to impose requirements, with DORA requiring financial entities to meet framework requirements by January 2025.
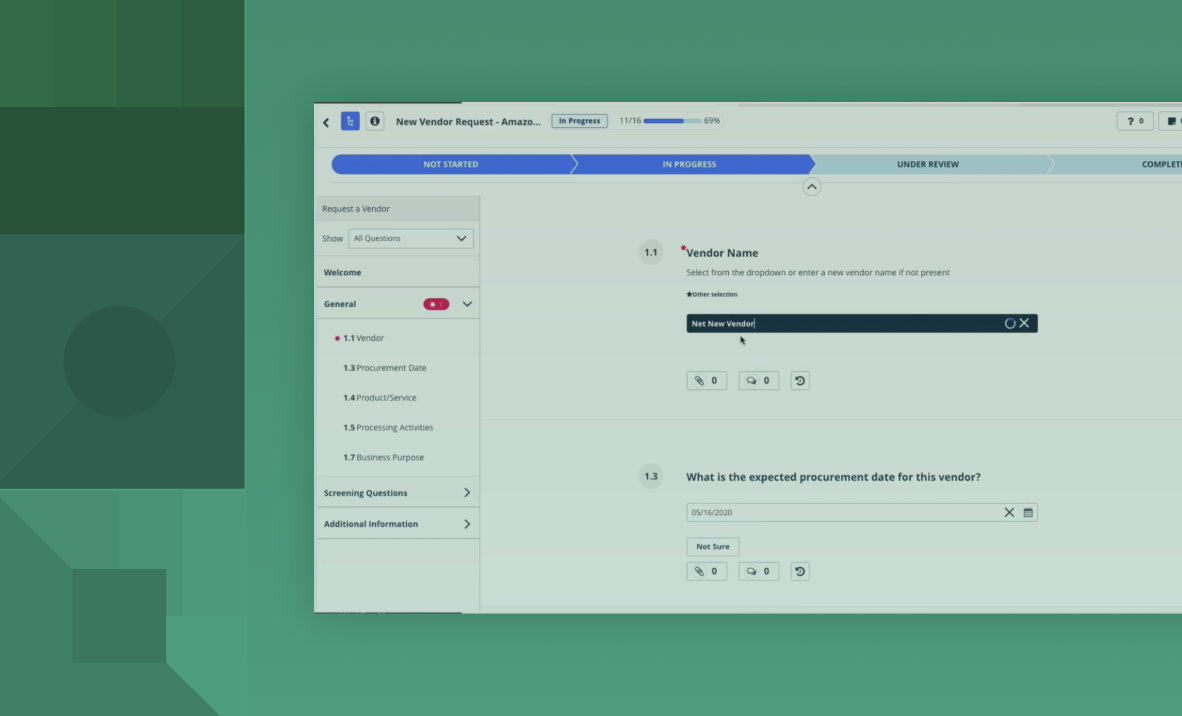
OneTrust offers robust capabilities that help organizations centralize the end-to-end risk management lifecycle to identify, mitigate, monitor, and analyze third-party and supply chain risks while driving risk-informed contracting workflows. Continuous monitoring through risk intelligence vendors can alert to weaknesses in ICT management, data breaches, and more across third and fourth parties.
The CrowdStrike outage has highlighted the need for more robust third-party operational risk management strategies. Watch this webinar to explore the lessons learned and gain actionable insights on fortifying your organization's defenses and promoting continuous operational resilience.