Difference between PCI DSS v3.2.1 and v4.0
Like previous versions, the new standard includes a list of 12 principal PCI DSS requirements tied to six key objectives. However, PCI DSS v4.0 has made substantial changes to the requirements, broadening the scope in response to the evolving payment landscape.
The table highlights key differences between the main requirements in PCI DSS v3.2.1 vs. PCI DSS v4.0:
| PCI DSS v3.2.1 | PCI DSS v4.0 | |
| Build and maintain a secure network and systems | 1. Install and maintain a firewall configuration to protect cardholder dat | 1. Install and maintain network security controls |
| 2. Do not use vendor-supplied defaults for system passwords and other security parameters | 2. Apply secure configurations to all system components | |
| Protect cardholder data | 3. Protect stored cardholder data | 3. Protect stored account data |
| 4. Encrypt transmission of cardholder data across open, public networks | 4. Protect cardholder data with strong cryptography during transmission over open, public networks | |
| Maintain a vulnerability management program | 5. Protect all systems against malware and regularly update antivirus software or programs | 5. Protect all systems and networks from malicious software |
| 6. Develop and maintain secure systems and applications | 6. Develop and maintain secure systems and software | |
| Implement strong access control measures | 7. Restrict access to cardholder data by business need-to-know | 7. Restrict access to system components and cardholder data by business need-to-know |
| 8. Identify and authenticate access to system components | 8. Identify users and authenticate access to system components | |
| 9. Restrict physical access to cardholder data | 9. Restrict physical access to cardholder data | |
| Regularly monitor and test networks | 10. Track and monitor all access to network resources and cardholder data | 10. Log and monitor all access to system components and cardholder data |
| 11. Regularly test security systems and processes | 11: Test security of systems and networks regularly | |
| Maintain an information security policy | 12. Maintain a policy that addresses information security for all personnel | 12: Support information security with organizational policies and programs |
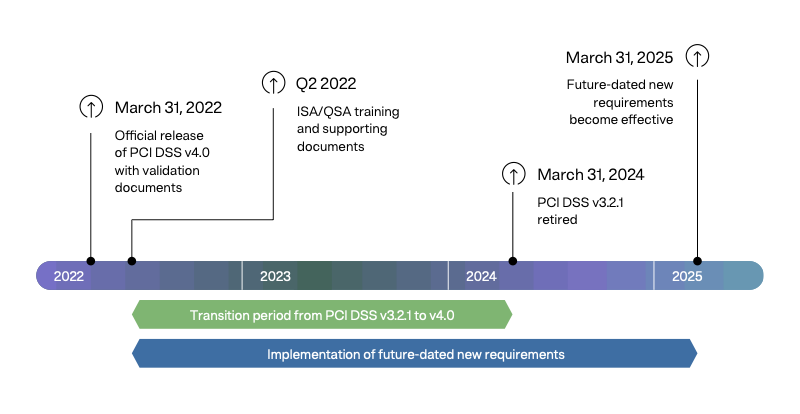
Under the 12 principal requirements, PCI DSS v4.0 introduces 64 new sub-requirements — 13 that should be implemented immediately for any PCI DSS v4.0 assessments (or at least by March 31, 2024), and the remaining 51 requirements to be enforced by March 31, 2025.
New ways to validate PCI DSS v4.0 compliance
A significant shift in PCI DSS v4.0 is its focus on outcomes rather than strict protocols. As long as an entity satisfies the standard’s requirements and objectives, it can implement security controls better suited to its operations.